Identification and Authentication Failures. Lets take a look at one of the most popular and devastating attacks on the OWASP Top 10.

Owasp Top 10 Security Vulnerabilities In 2021 Debricked
The OWASP Top 10 - 2017 is based primarily on 40 data submissions from firms that specialize in application security and an industry survey that was completed by over 500 individuals.
. The OWASP Top 10 does not address all possible vulnerabilities but it accurately identifies the most common and most critical web application security risks. The OWASP is a not for profit charitable organization focused on making security visible by providing impartial practical security advice for web applications. Categories in the Common Weakness Enumeration CWE group entries based on some common characteristic or attribute.
Weaknesses in this category are related to the A04 Insecure Design category in the OWASP Top Ten 2021. The Open Web Application Security Project foundation OWASP publishes a version every three years. 12 The OWASP Top 10 Application Security Risks The OWASP Top 10 Application Security Risks A1 Injection Injection flaws such as SQL OS and LDAP injection occur when untrusted data is sent to an interpreter as part of a command or query.
Its the standard that everyone uses to test their applications. The OWASP Top 10 vulnerabilities 2021 explained. OVERVIEW OF THE OWASP TOP 10 RISKS 12345 Injection Broken authentication Sensitive data exposure XML external entities Misconfiguration Broken access control Cross-site scripting Insecure deserialization Vulnerable components Insufficient logging.
The OWASP Top 10 is a technology agnostic guide for managing common web application security risks. Adding three new categories. OWASP collects data from companies which specialize in application security.
If you want a summary of the categories of the latest edition keep on. It also explains how to generate and save the OWASP Top Ten 2013 Report in Invicti Enterprise and Invicti Standard. An attacker injects malicious code into an interpreter usually through an input field in order to gain access to information or damage a system.
This topic describes the OWASP Top Ten 2013 Report sections. Ad Your code is more secure with SonarQube to automatically detect OWASP vulnerabilities. The OWASP Top Ten Proactive Controls 2018 is a list of security techniques that should be considered for every software development project.
In summary the OWASP Top Ten consists of. This document is written for developers to assist those new to secure development. Meet with your penetration testing team to conduct a pentest based on recent updates in the OWASP top 10.
Its data spans vulnerabilities gathered from hundreds of organizations and over 100000 real-world applications and APIs. The OWASP Top 10 was first published in 2003. Security feedback during code review is your opportunity to learn feel more engaged.
For nine years the OWASP Top 10 has been the standard for web application security. 11 rows Intended first as an awareness mechanism the Top 10 covers the most critical web application. The original idea behind OWASP Top 10 is spreading awareness and not creating some type of standard.
The OWASP Top 10 is the de-facto guide for security practitioners to understand the most common application attacks and risks. OWASP Top 10 is a standard awareness document for developers and web application security. Top 10 Overview Malicious Injection.
In this OWASP Top 10 training series you will practice the exploitation of most OWASP Top 10 vulnerabilities both in Java and NodeJs. Since 2010 OWASP solicits data from information security professionals and uses it to develop a list of the top 10 most critical security risks in web application security. The OWASP Top Ten 2013 Report helps organisations identify listed vulnerabilities.
Security Logging and Monitoring Failures. There are many benefits to OWASP penetration testing that can help protect your company from financial loss data theft or simply safeguarding your firms reputation while also making the website. Vulnerable and Outdated Components.
It is very frequently referred by security professionals and web application developers. Injection attacks operate on the principle of submitting injecting malicious content or code into a web application. The OWASP Top 10 Vulnerabilities are.
Part of these changes include. The OWASP Top Ten is a classification of the most common web application security risks and should be used as a guide when performing penetration tests on your web application. You will learn how to leverage the power of the best web proxies and you will understand why you were able to exploit the vulnerabilities.
The Top 10 items are selected and prioritized according to this. Injection attacks are actually a wide range of attacks with similar core functionality. Changing the name and scope of old categories.
This data spans vulnerabilities gathered from hundreds of organizations and over 100000 real-world applications and APIs. The OWASP Top 10 ranks the ten most severe security risks. The OWASP Top 10 Vulnerabilities.
Consolidating old categories into newer or existing ones. All of OWASPs materials are free and open source. OWASP released its newest Top 10 version on September 24 2021.
OWASP Top 10 training summary. An insecure authentication system allows attackers to impersonate other users. Software and Data Integrity Failures.
The OWASP Top 10 is a standard document which consists of the top ten of the most impactful web application security risks in the world.
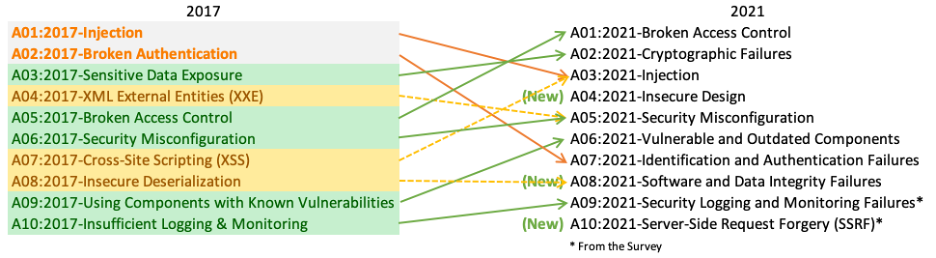
What Is Owasp What Are Owasp Top 10 Vulnerabilities Imperva

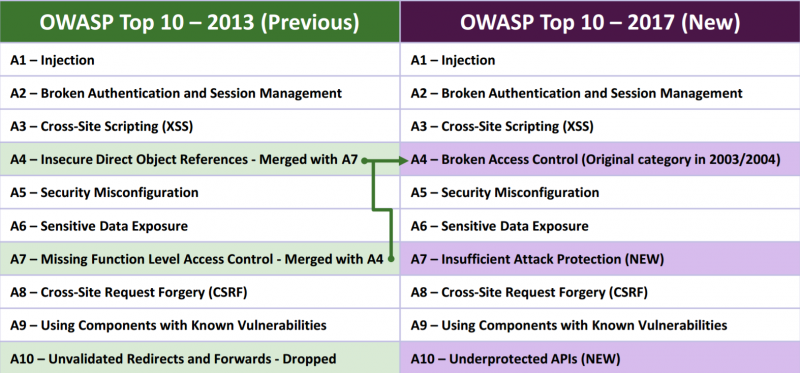
An Overview Of Owasp Top 10 2017 Dionach
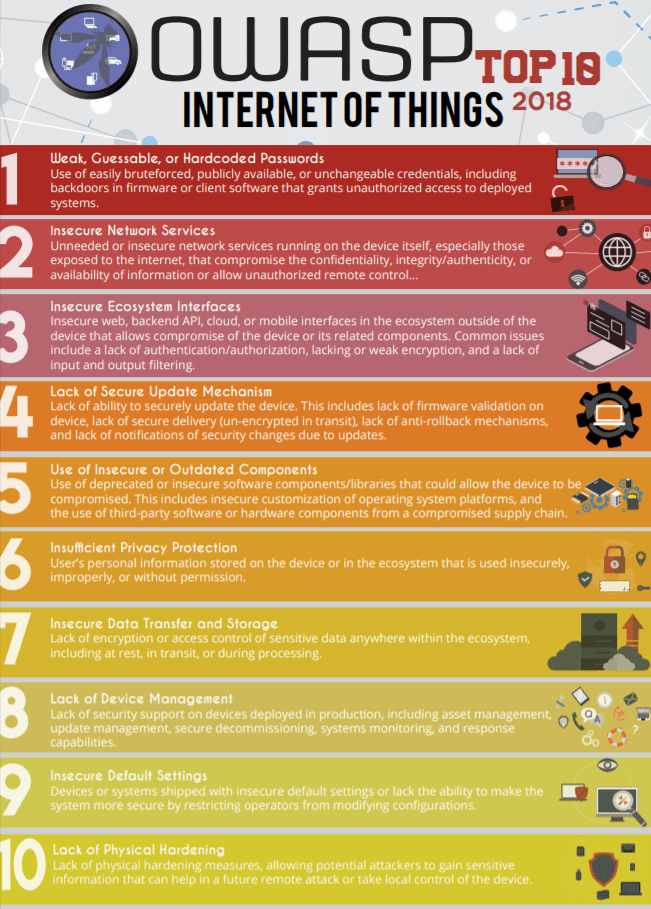
The Owasp Iot Top 10 List Of Vulnerabilities Infosec Insights
0 Comments